Mission
Making sure all our clients sleep well obviously does not end with a fully secure and operational data center. We have been delivering our services for long enough to know that information we are working with on daily basis for the past decade have to be handled with the utmost importance.
We are happy to say there has never been a breach or similar unpleasant situation. If we can expect it, we will prevent it. We would not be surprised if such a statement would not be enough for all our valued clients, though. You are more than welcome to explore what do we do in order to protect your data, privacy, and business overall.
Logins
The matter of security starts with users themselves. We are more than happy and capable of protecting your data, but we sure need you to cooperate on that. Knowledge and awareness are the key.
We would like to suggest taking following actions, even though most of the clients are well aware of them. Better safe than sorry.
- Set up individual login credentials for each user,
- Set up two factor authentication - 2FA is fully supported on all our deployment solutions,
- Do not share passwords with anyone – especially not online,
- Follow a set of rules when setting up (or changing) your passwords:
- 11+ characters,
- change them (at least) once a year,
- do not „recycle“ old passwords,
- avoid using the same text as both username & password,
- make sure user’s account is deactivated after the person is suspended,
- generate a new password and an API key when you think the old one might be compromised,
- make sure users change their credentials themselves and do not use emails or chats for that.
Easy Software products come with the option of a mandatory change of users‘ passwords on regular basis (one of seven time periods to choose from). That obviously does not end there, though. We included the option to set the required length of users‘ passwords to accommodate our clients‘ needs.
As previously mentioned 2FA is fully supported on all our deployment solutions, further information are available on this documentation page.
Storage space
Having thousands of clients allowed us to monitor the overall usage of their storage space to make sure all clients will not suffer from the lack of megabytes. Clients are provided with 50GB of storage space for every application.
However, we want to make sure all clients are taken care of. If you need to keep saving files of larger sizes, do not hesitate to contact your Account Manager or send an email to salesteam@easysoftware.com. Our team will always be happy to take over and make that happen.
Backups
Nobody can predict the unpredictable. We are no different from other companies in this, as we too have to accept the fact that problems can occur – no matter how low such a risk is. Data reach will be mentioned below but first there needs to be a process put in place that guarantees clients‘ data will never be deleted.
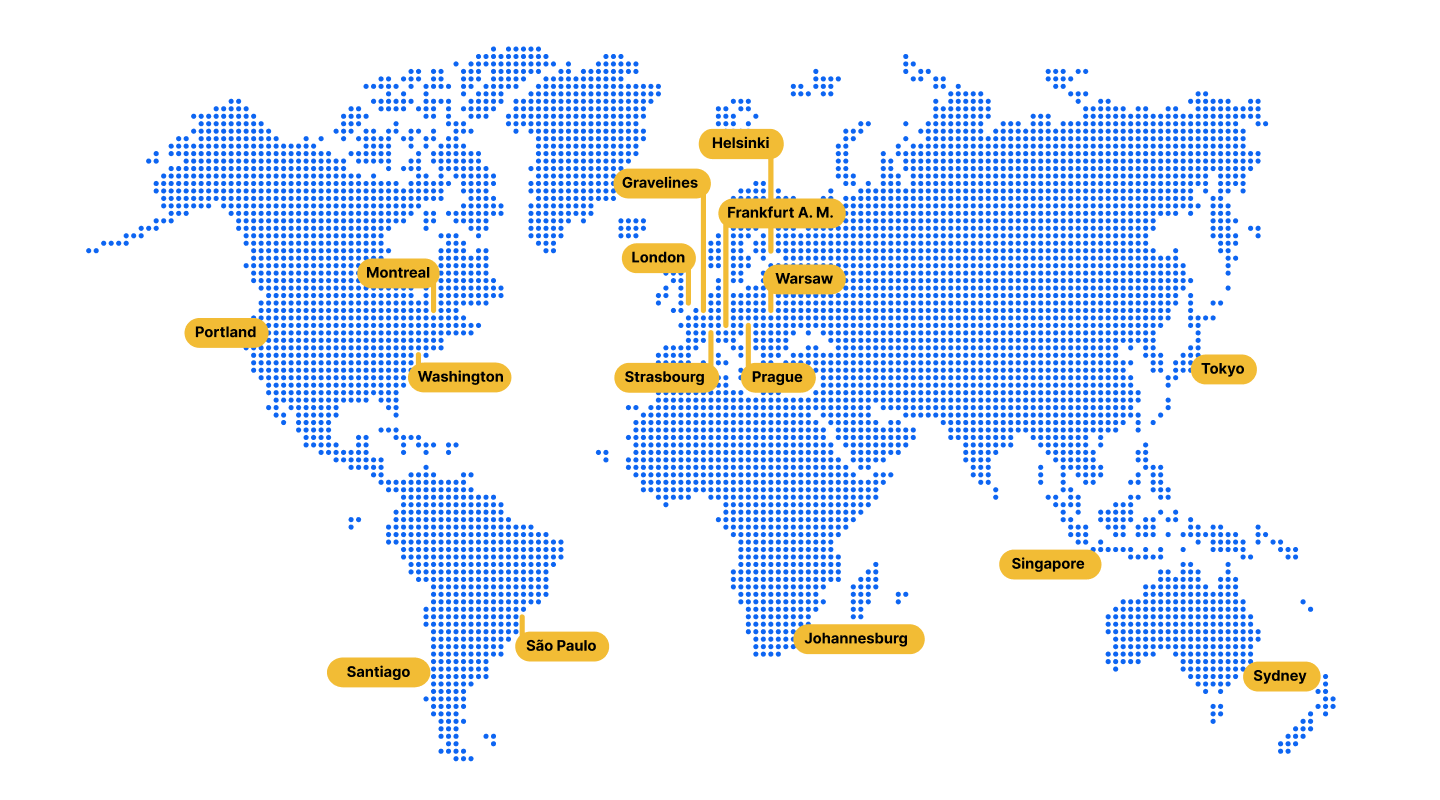
Working with data centers that are geographically distant from each other also allows us to make sure all backups are always stored in multiple locations. This works as a great prevention from natural disasters and represents yet another step towards making sure our hosting will never fail.
Database backups are created every 2 hours. For the most recent two days, every backup is stored. From 3+ days in past, only one backup per day is stored. Backups of attachments (files) are created every 24 hours. It is important to us to provide our clients the option to perform a rollback if requested, so those backups are saved for 33 days after being created.
Backups are encrypted both during the transfer and while stored on physical discs.
Data reach
Everything is connected. The overall system is only as strong as its weakest link and we are well aware of it. All our backups and promises would not mean anything if we were not able to get our clients up and running in a short amount of time. Should any major problem occur, the database itself can be uploaded back within 15 minutes from the moment our server admins start the process. A separate upload of files is happening simultaneously as it is crucial to us to provide a working application as soon as possible. The time it takes to migrate all clients‘ files can take a few minutes longer as it largely depends on the total size. The migration of 10GB of files takes about 15 minutes.
99.9% long-term uptime has been achieved on regular basis.
Failover
Being able to replace a piece of hardware that malfunctioned in a quick manner is just as important as the rest when making sure clients‘ continuity is taken care of. Data is stored on a RAID 1 storage node mirroring on two discs. The application keeps running as long as there is at least one disc working.
We also have whole backup machines ready for deployment in case of irreparable damage on an existing one.
Data privacy
Users‘ access to the application is limited by permissions set within the system. This part of our products is very complex, as it is a necessary part of a proper project management. Cross-site scripting (XSS) prevented where required, the rest is handled by mentioned permissions.
Any access to the application goes through a tunneling protocol (SSL) while the database is stored on an encrypted disc. SSH-2 encryption is used for the backup transfer.
Only HTTP and HTTPS accesses are allowed through our firewall system. Every HTTP request is immediately redirected to HTTPS as well.
Permanent support & maintenance
Clients hosted on our cloud receive numbers for our server hotline that is operational 24/7. However, we want to stress that this line serves for critical issues caused by our side. Calling this number for other purposes might result in losing the approval to use it.
It goes without saying that all applications are constantly monitored and immediate reports are generated in case of any issues. This allows us to resolve the majority of problems without even affecting the end user.
Such monitoring does not concern applications only. All hardware is also under control at all times. This is essential for larger clients as we are able to suggest performance upgrades before users start experiencing higher response times of the application – making for an optimized configuration for every client.
These services, together with the initial setup and continuous administration, are included in the standard price for private clouds. You can find that on our pricing pages or reach out to your Account Manager and request further information.
Infrastructure maintenance windows
On a monthly basis, the infrastructure is updated with the latest optimizations and security patches. Additionally, ad-hoc updates may be implemented based on unforeseeable events. This process is an absolute necessity for all cloud service providers to ensure stability and safety on the highest possible level. Such updates require so-called planned maintenance windows, which are night hours when the servers (and their applications) may not be accessible. This, of course, does not cause any data loss.
In Easy Cloud the maintenance windows are 1 am - 4 am in the time zone of your data center (see map above). If you wish to move your application to a different time zone, just contact our support.
The dynamic world of cloud IT requires quick and flexible reactions to significant news. Therefore, an update may be required as soon as possible without the possibility to inform users in advance. We guarantee that the operation is done in this time frame. And we always do our best to keep downtime as short as possible.
Flexibility
We have always been fans of flexibility, both in products and services. Explore how can the hosting be modified, if you choose to be hosted on our Private Cloud.
We have been approached with requests of VPN a few times in the past. However, after several consultations with such clients, we have always agreed that it would not bring any extra usage, as HTTPS already serves the same purpose more effectively. We still understand that it might represent a strict requirement in some cases, so this service can be provided on our Private Cloud. Reach out!
GDPR compliance
Data security, as described above, is sufficient according to GDPR requirements and recommendations
Please note that Easy Software does not control data of Easy Software‘s clients. Hence, according to our Terms & Conditions, our clients may comply with GDPR on the level of data collected in Easy Software products. Breach of this may result in immediate discontinuity of service.
Easy Software products provide users with all tools to limit, erase or delete data upon request, as required by GDPR.
Please note that upon official request Easy Software may become obliged to limit, erase or delete data. Easy Software policy is to provide enough time to clients to perform necessary actions before Easy Software has to perform obligatory data changes directly.
Data centers
Multiple high-end data centers, all fulfilling parameters in the following description
Every data center holds appropriate certifications
Geographically distant data centers to prevent permanent damage from natural disasters
Barbed wires, surveillance & security systems in place
Restricted access, thorough verification system & 24/7 human presence on site
Two separate electrical power supplies, two network connections & network rooms
Security of facilities
Even though it is highly unexpected there would be any attempt to breach these facilities, we see it as our duty to make sure clients‘ data are always secure. All access to data centers are strictly monitored and every boundary of the property is secured using barbed-wire fencing. This, together with a video surveillance and movement detection systems, is designed to prevent any intrusions. The security team is on site 24/7 to support all the technology set up to guarantee proper safety.
Staff members have to follow strict security procedures. Every employee receives a RFID name badge that restricts their access and permissions and is required before passing through security doors. Access rights are reassessed on regular basis.
Electrical supply and network
Two separate electrical power supplies power data centers, equipped with UPS devices (250 kVA per device) and backed-up by generators with an initial autonomy of 48 hours to make sure servers are always accessible. Some of the server ranges are also equipped with double power supplies and double network cards, making sure the infrastructure is redundant from end to end.
Fibre optic network is deployed across the globe with cutting-edge technology that is installed and maintained by in-house teams of engineers. It was also chosen to build the network in a totally redundant manner where multiple security measures have been put in place, in order to eliminate any risk of failure or serious issues. Such redundancy allows clients‘ data to take the shortest path and noticeably lower the overall response time.
At least 2 separate network connections are maintained within each data center to prevent any issues resulting from a providers‘ outage. There are also 2 network rooms capable of taking over from one another to serve the same purpose.
Certifications
It is understandable that clients require multiple certifications as a proof of the data center’s capability of keeping their data safe. Here is a list of certifications that our data centers hold:
- PCI DSS Level 1
- ISO/IEC 27001:2013
- SOC 1 Type II and SOC 2 Type II
- Cloud Security Alliance (CSA) STAR self-assessment
Furthermore
Heat and fire have always been an enemy of high-performing technologies. It is very important to stay out of trouble by having every room fitted with a system that detects and extinguishes fire immediately. All data centers comply with APSAD R4 rule and N4 conformity certification.
Majority of hosting rooms are also free from air conditioning and have water cooling installed instead. This system disperses 70% of the emitted heat, while the air cooling takes care of the rest. This led to energy costs being halved, making for a more ecological way of work.
For more information, please check out Private Cloud.